Understanding the Importance of Critical Data Management
Written on
Chapter 1: The Necessity of Identifying Critical Data
Are you aware of your critical data? If you haven’t yet pinpointed your critical data, it’s crucial to read this article and start your efforts promptly.

Photo by Ernestine Casten on Unsplash
With the emergence of data protection regulations such as GDPR and KVKK, a consensus is forming around best practices for acquiring, processing, sharing, and safeguarding data, particularly personal information. The capability for data governance is one of the most significant indicators of a company's maturity in understanding these practices. In this section, I’ll explore how to identify critical data, which is a fundamental step in data governance, by posing several questions.

Initially, we must ascertain the location of our data. A decade ago, organizations found it straightforward to track their data as it resided on local servers at their main offices. Nowadays, many companies utilize a mix of public and private clouds, local servers, and hybrid solutions, leading to improved efficiency but complicating data visibility. We often lack clarity on data origins, departmental usage, storage methods, and reception channels. Significant efforts are required to uncover these details. File auditing tools have been instrumental in revealing the locations and transfer pathways of files, yet we also need to determine who has access to this data and who is accountable for it. This process begins with gathering cross-departmental data repositories. While IT teams have some awareness of available data, it’s essential for personnel from sales, marketing, and legal to identify the data and databases they utilize.
What Constitutes Critical Data?
Thanks to robust regulatory frameworks such as GDPR/KVKK, there is now widespread agreement on the necessity of safeguarding personal data, which includes names, addresses, phone numbers, identity numbers, credit card details, and birth dates of employees and customers. But what exactly is critical data?
DAMA International (the Data Management Association) defines critical data as that which is essential for success in a specific business domain. Alternatively, critical data can also be seen as the information necessary to achieve desired outcomes in critical processes. This interpretation is based on my insights derived from various sources I've studied and engaged with.
In response to a previous inquiry about what constitutes critical data, I outlined that any data set whose confidentiality is compromised, integrity is violated, or accessibility is obstructed can severely disrupt business operations or create significant compliance gaps. How does this definition resonate with the principles of the CIA Triad?
The Importance of Identifying Critical Data
To effectively manage our data, we must first understand its location. Organizations today face an overwhelming influx of information. A decade ago, data was easier to locate because it was stored on-site. Today, businesses employ a variety of storage solutions, including public and private clouds, which complicate our understanding of data flows, usage, and storage practices.
Organizations exist to create value for their stakeholders through various business processes carried out by different functional units such as Human Resources, Accounting, Marketing, Sales, and IT. Each of these units maintains databases containing data necessary for their functions. While IT professionals may have some awareness of the data landscape, it’s vital for other departments to identify the data they rely on.
This discovery process requires substantial effort. File auditing tools have been helpful in pinpointing file locations and transfer points, but we also need to clarify who has access to data and who bears responsibility for it. We started by collecting data repositories across the business.
The efficiency of data processing plays a crucial role in realizing the expected value from the organization. This efficiency must be balanced across people, processes, and technology. Relevant roles should be clearly defined, tasks assigned, measurable goals established, and data governance technologies integrated into the system.
To make swift and informed decisions regarding which data to retain, delete, or share, we need established criteria. I contend that the degree of criticality is paramount in this decision-making process.

Photo by Joanna Kosinska on Unsplash
Examples of Critical Data
When asked about examples of critical data, I think of the following:
- Personal data of employees, customers, service providers, and business partners under GDPR/KVKK.
- Audit reports, internal controls, and risk management documentation.
- Reports detailing cyber vulnerabilities, including penetration tests.
- Financial data about the company’s structure.
- Intellectual property and information regarding products and services in development.
- Data concerning senior management or key personnel.
Determining Critical Data
There can be varying opinions among business units regarding data processing priorities, leading to a lack of consensus on what data is deemed critical. Some data may only be vital for a specific team's functions, and what is critical for one process may not hold the same value for another. Thus, it’s essential to manage data according to its highest criticality for any given process. This necessity justifies significant efforts to secure relevant data.
Mature organizations often employ data criticality weighting systems to emphasize what matters most in data governance. Below are key considerations for determining data criticality:
- Purpose of data processing.
- Legal, financial, and reputational risks associated with data confidentiality, integrity, and accessibility.
- Number of stakeholders relying on the data.
- Frequency of data processing across various processes.
- Current legal obligations regarding data storage and destruction.
- Future project data requirements, including notification obligations.
Evaluating these factors aids in establishing varying criticality levels for data, ranging from the most crucial to those only critical in specific contexts.
It’s important to note that definitions of critical data can evolve over time. As new data types emerge, previously critical data may lose its significance. Ideally, organizations should regularly update their definitions of critical data.

Photo by Christopher Ott on Unsplash
The first step in identifying critical data involves recognizing critical business processes. A critical business process is defined as the essential activities required to generate expected organizational value. For instance, in an online retail context, a critical process would be the steps a potential customer takes to complete a purchase, including entering payment details and confirming the transaction.
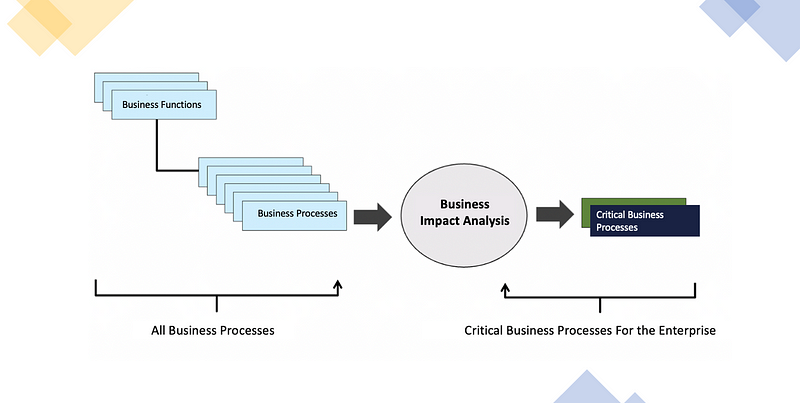
Designed and prepared by Gokhan Polat
In addition to identifying critical processes, it is vital to engage with managers from internal audit, risk management, compliance, and legal departments to compile a list of critical data for the organization. The data fields identified during the GDPR/KVKK compliance inventory should also be included in this list, yielding an initial draft of critical data types. This process raises awareness among relevant units about the significance of critical data, facilitating more consistent input for our list.
Next, we need to determine where this identified data resides. For this, data discovery technologies are essential. Tools for data loss prevention (DLP) and data classification can assist, but I’ve observed their limitations firsthand. Specialized technologies are necessary for effective data discovery.
Once we have identified critical data and their storage locations, we can evaluate the security level of current controls surrounding these critical areas. This evaluation should be accompanied by the establishment of a data classification policy that incorporates confidentiality, integrity, and accessibility principles across the organization.
Photo by Moritz Kindler on Unsplash
Consequences of Failing to Identify Critical Data
From a risk management perspective, risk embodies uncertainty regarding future events, encompassing both opportunities and threats. Adequate preparation allows for effective risk management, while unpreparedness magnifies vulnerabilities and leads to significant challenges.
Neglecting to identify critical data can lead to several adverse outcomes:
- Unnecessary expenses in processing and maintaining low-criticality data.
- Storing critical data, possibly alongside unclassified data, in environments with insufficient security controls.
- Breaches of the need-to-know principle due to inadequate access restrictions to critical data.
- Data breaches triggered by cyber-attacks targeting critical data.
- Inaccurate analysis results due to unreliable data.
- Disruptions in processes associated with critical data.
It's Time to Act to Safeguard Your Critical Data!
The protection of critical data is imperative. However, determining the extent and methods of security measures hinges on budget and resource allocation. Ensuring the security and integrity of critical data involves costs. How much are you prepared to invest in safeguarding this data?
The risks we encounter are continually evolving, necessitating the adoption of new hardware and software solutions to enhance our control environment or optimize existing infrastructure. Following the identification of critical data, readiness to invest in the necessary systems and infrastructure for its protection is essential. The costs of inadequate control measures will far exceed the investment needed to establish an appropriate technological framework for your business.
This video delves into the significance of critical data elements and the extent of data retention required for effective governance.
In this video, we discuss the prevalent issue of missing critical data in online narratives and explore the implications of this oversight.
Gokhan Polat - Seminar Leader on Information Security Management Systems and Auditing...
Being a highly motivated professional, I thrive on achieving successful outcomes through collaboration with strong teams.
www.linkedin.com
More…
How To Reduce Cyber Risks
A robust control environment tailored to cyber risks necessitates a clear understanding of the functions of the controls in place.
What does Zero Trust Architecture Stand For?
This article explores the concept of Zero Trust Architecture and its implications for data security.
Port Scanning Techniques Using Nmap
This article was created for METU's Operating Systems (510) course, with all rights reserved.